Ad hoc modification information
Home » modification » Ad hoc modification informationYour Ad hoc modification images are available in this site. Ad hoc modification are a topic that is being searched for and liked by netizens now. You can Download the Ad hoc modification files here. Download all royalty-free photos.
If you’re searching for ad hoc modification images information linked to the ad hoc modification interest, you have visit the right site. Our site frequently provides you with hints for viewing the highest quality video and picture content, please kindly hunt and locate more informative video content and graphics that match your interests.
Ad Hoc Modification. Leplin 1975 has argued against the received view of ad hoc reasoning that unobservability in principle mitigates the condition of being de facto unobservable. Iv What is the main draw-back of Poppers method of falsification. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. The method of claim 1 further comprising.
 Definitions Of Ad Hoc Decision Making Categories And Examples Download Table From researchgate.net
Definitions Of Ad Hoc Decision Making Categories And Examples Download Table From researchgate.net
Archived Forums Windows 10 Networking. In ad-hoc processes and in case management in general the ideal is not to model the complete casuistry in an explicit way as in the previous example but to model the behavior from the point of view of the case. Iv What is the main draw-back of Poppers method of falsification. How then can we distinguish between an authentic and inauthentic ad hoc modification Chalmers 1999 p75. And a system for adding the ad hoc task to the existing. Ie in a WfMS with partitioned.
Creating an additional ad hoc task.
Ad hoc modifications of quantum electrodynamics are discussed with special reference to the restrictions imposed by charge conservation. From the Cambridge English Corpus It requires complex processes to track and record the thousands of ad hoc messages phone calls memos and conversations that comprise much project-related information. Leplin 1975 has argued against the received view of ad hoc reasoning that unobservability in principle mitigates the condition of being de facto unobservable. Define Explain Describe Identify. It is dealt with by some ad hoc modifications of the grammar operations. Creating an additional ad hoc task.
 Source: slideplayer.com
Source: slideplayer.com
Ad hoc modifications of quantum electrodynamics are discussed with special reference to the restrictions imposed by charge conservation. Ad Hoc IP Range Modification for Windows 10. A system for modifying a computer-executed process the system comprising. Iv What is the main draw-back of Poppers method of falsification. Indeed the failure to detect X is less damaging.
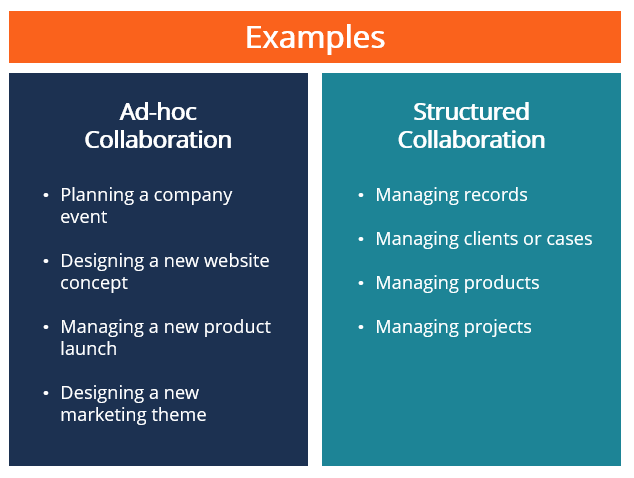 Source: corporatefinanceinstitute.com
Source: corporatefinanceinstitute.com
Analyze an argument argument. Ad Hoc IP Range Modification for Windows 10. A system for creating an ad hoc task for inclusion in an existing process. It is dealt with by some ad hoc modifications of the grammar operations. Sunday June 18 2017 628 PM.
 Source: researchgate.net
Source: researchgate.net
In ad-hoc processes and in case management in general the ideal is not to model the complete casuistry in an explicit way as in the previous example but to model the behavior from the point of view of the case. Indeed the failure to detect X is less damaging. Evaluate an argument experiment. Ad hoc modifications of quantum electrodynamics are discussed with special reference to the restrictions imposed by charge conservation. Continuing with the previous example it would be better to include in the form the Revision options.
 Source: researchgate.net
Source: researchgate.net
Iv What is the main draw-back of Poppers method of falsification. Creating an additional ad hoc task. For the first time this paper presents methods which allow ad-hoc modifications eg to insert delete or shift steps to be performed in a distributed WfMS. By systematically investigating ad hoc modifications in protocol-driven interventions new opportunities exist to identify the extent and impact of both anticipated and unanticipated modifications. Iii How does Popper apply his above-mentioned views regarding the ad-hoc modifications of theories to show that Karl Marxs theory on the evolution of societies is pseudo-science.
 Source: researchgate.net
Source: researchgate.net
A system for accessing the existing process. By systematically investigating ad hoc modifications in protocol-driven interventions new opportunities exist to identify the extent and impact of both anticipated and unanticipated modifications. A system for modifying a computer-executed process the system comprising. Indeed the failure to detect X is less damaging. And a system for adding the ad hoc task to the existing.
Source:
Creating an additional ad hoc task. How then can we distinguish between an authentic and inauthentic ad hoc modification Chalmers 1999 p75. It is dealt with by some ad hoc modifications of the grammar operations. Continuing with the previous example it would be better to include in the form the Revision options. Define Explain Describe Identify.
 Source: slideplayer.com
Source: slideplayer.com
The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. Indeed the failure to detect X is less damaging. Ad hoc modifications may occur at various stages of the implementation process. Sunday June 18 2017 628 PM. Define Explain Describe Identify.
 Source: sciencedirect.com
Source: sciencedirect.com
How then can we distinguish between an authentic and inauthentic ad hoc modification Chalmers 1999 p75. Define Explain Describe Identify. Ii Explain briefly the views of Karl Popper regarding Ad-hoc modification of theories. The method of claim 1 further comprising. Ad hoc modifications of quantum electrodynamics are discussed with special reference to the restrictions imposed by charge conservation.
 Source: logicallyfallacious.com
Source: logicallyfallacious.com
As many of the examples of ad hoc reasoning we have reviewed rely on unobservable entities and forces one may wonder whether unobservability has any bearing on the accusation of adhocness. Ad Hoc IP Range Modification for Windows 10. The method of claim 1 further comprising. Analyze an argument argument. Ie in a WfMS with partitioned.
 Source: independent.academia.edu
Source: independent.academia.edu
A system for modifying a computer-executed process the system comprising. Such ad hoc modification would completely destroy any progress in scientific discovery. Ad hoc modifications may occur at various stages of the implementation process. Archived Forums Windows 10 Networking. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory.
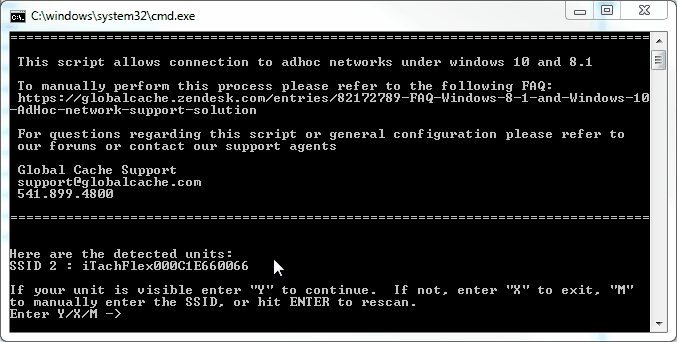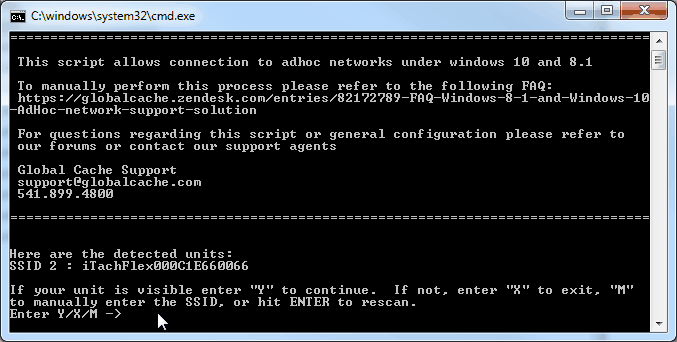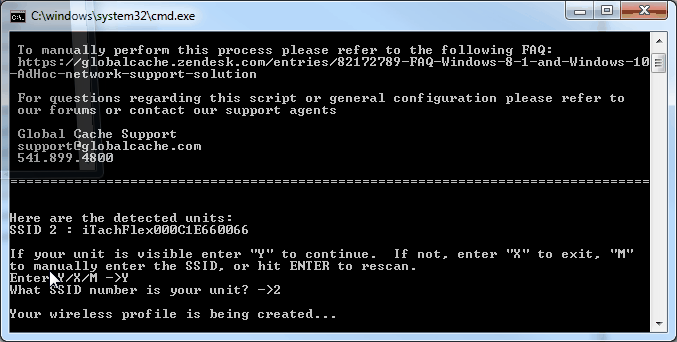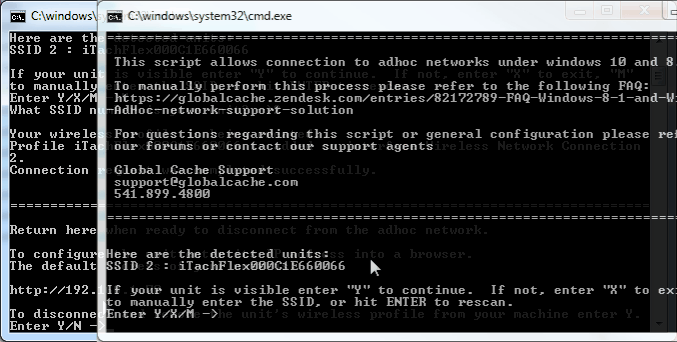 Source: globalcache.zendesk.com
Source: globalcache.zendesk.com
The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. Iv What is the main draw-back of Poppers method of falsification. Leplin 1975 has argued against the received view of ad hoc reasoning that unobservability in principle mitigates the condition of being de facto unobservable. A system for creating an ad hoc task for inclusion in an existing process. As many of the examples of ad hoc reasoning we have reviewed rely on unobservable entities and forces one may wonder whether unobservability has any bearing on the accusation of adhocness.
 Source: researchgate.net
Source: researchgate.net
Define Explain Describe Identify. In this example the modification cannot be falsified so it does not tell us anything new about the world. A system for creating an ad hoc task for inclusion in an existing process. Ad Hoc IP Range Modification for Windows 10. Ad-hoc processes modeling.
 Source: pinterest.com
Source: pinterest.com
The method of claim 1 further comprising. Archived Forums Windows 10 Networking. Ii Explain briefly the views of Karl Popper regarding Ad-hoc modification of theories. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. From the Cambridge English Corpus It requires complex processes to track and record the thousands of ad hoc messages phone calls memos and conversations that comprise much project-related information.
 Source: researchgate.net
Source: researchgate.net
Ad Hoc IP Range Modification for Windows 10. Ii Explain briefly the views of Karl Popper regarding Ad-hoc modification of theories. By systematically investigating ad hoc modifications in protocol-driven interventions new opportunities exist to identify the extent and impact of both anticipated and unanticipated modifications. Ad-hoc processes modeling. Already set ScopeAddress to desired IP but the ad-hoc still giving away 192168137024 the default IP range.
 Source: slideplayer.com
Source: slideplayer.com
By systematically investigating ad hoc modifications in protocol-driven interventions new opportunities exist to identify the extent and impact of both anticipated and unanticipated modifications. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. And a system for adding the ad hoc task to the existing. A system for creating an ad hoc task for inclusion in an existing process. From the Cambridge English Corpus It requires complex processes to track and record the thousands of ad hoc messages phone calls memos and conversations that comprise much project-related information.
 Source: researchgate.net
Source: researchgate.net
A system for modifying a computer-executed process the system comprising. Indeed the failure to detect X is less damaging. A system for modifying a computer-executed process the system comprising. Iv What is the main draw-back of Poppers method of falsification. A system for creating an ad hoc task for inclusion in an existing process.
 Source: researchgate.net
Source: researchgate.net
Archived Forums Windows 10 Networking. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory. Ie in a WfMS with partitioned. Ad Hoc IP Range Modification for Windows 10. Define Explain Describe Identify.
 Source: researchgate.net
Source: researchgate.net
Define Explain Describe Identify. Ad-hoc processes modeling. How then can we distinguish between an authentic and inauthentic ad hoc modification Chalmers 1999 p75. Define Explain Describe Identify. The received view of an ad hochypothesis is that it accounts for only the observations it was designed to account for and so non-ad hocness is generally held to be necessary or important for an introduced hypothesis or modification to a theory.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title ad hoc modification by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.
Category
Related By Category
- Leatherman modification ideas
- Organizational behavior modification theory ideas
- Seamoth modification station location information
- Custody modification reasons information
- Kak shockwave modification information
- Subnautica cant place vehicle modification station information
- Loan modification while in chapter 13 information
- Behavior modification is based upon the principles of rewards and punishments advanced by ideas
- Modification lawyer information
- Z4 modification information